Learn about three key areas you need to think about as a CISO, and develop a plan for strengthening your information security program.
(I originally wrote this article for GitGuardian’s blog)
Introduction
You may have found this article for several reasons. Maybe you just landed a big promotion to CISO/CSO or you’re looking to become one soon. You could have been a CISO or security lead for a while now and are looking for new ideas. Whatever brought you here, you will come away with a game plan for strengthening your information security program.
First and foremost, a CISO is an advocate for good information security practices within the business. Stating it like that makes it sound simple, but there are so many responsibilities and considerations that go into a complete information security program. Security considerations go far beyond just technical controls. The many domains of cyber security could be listed along with key components of each, but it’s much easier to provide a graphic published by current CISO that organizes them into a map.
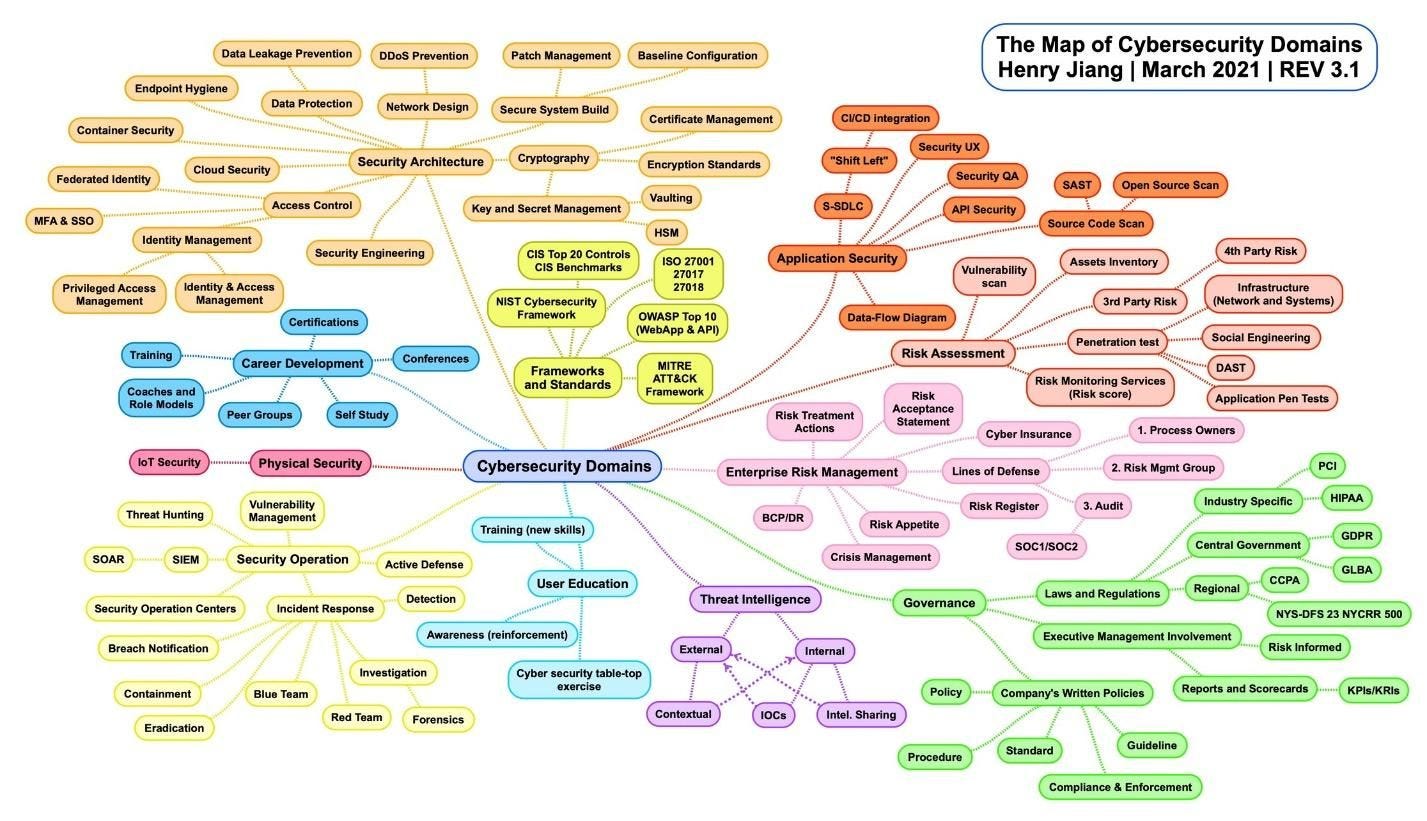
Cybersecurity Domain Map
Henry Jiang, Cybersecurity Domain Map ver 3.1
There’s a lot going on in this graphic, so let’s break it down. For the most part, it shows that most parts of cyber security can be grouped into the following broader domains: physical security, governance, risk assessment, enterprise risk management, threat intelligence, security architecture, user education, security operations.
Each broader domain has its own practices and considerations that get more granular. From the graphic above, it’s clear there are many things to take into consideration for an information security program. As a CISO/CSO you need to understand the purpose of each responsibility or control so you can effectively weigh the cost of implementing a program against the risk it is designed to mitigate.
This leads to the most overlooked side of a CISO’s role: their responsibility to the business and its profit. As an executive-level role, a CISO has a seat at the table that is making the most critical business decisions. In that position, you need to be the mediator between profit and risk. At some point, additional security controls or practices may be cost or productivity prohibitive which can adversely affect the business. You need to be able to recognize when your business needs growth in an area of information security, and you also need to be able to communicate your decisions effectively to the other executives and the board.

With all that responsibility, it might feel overwhelming to try to figure out where to begin. To help narrow things down and guide future action, you should focus on three main things in your first 90 days. First, you should understand the other leaders in your company and their awareness of and appetite for security. Second, you should plan to drive a security-minded culture within your organization. And lastly, you, of course, need to evaluate the technical side of your business’s current information security program. With all of those covered, you should be ready to tackle some big positive changes for your company.
Leadership’s relationship with information security
Information security solutions and programs need to be properly manned and implemented, and to that end you need to be able to effectively communicate the business’s security needs to leadership. People who don’t have a background in information security may have widely varying thoughts about it. Business executives are no exception. One of the first things you should do as CISO is gauge your board of directors’ initial concerns and priorities.
During the interview process to become a CISO, you will probably already get a pretty good idea of your business leaders’ awareness of information security risks. Odds are they are aware of big threats like ransomware but are they concerned about other topics like developing secure software or third-party risk? Ransomware clearly poses an immediate financial risk to a company, but things like brand perception, laws/regulations, and intellectual property loss are also likely to be impacted by various types of cyber threats. Understanding your business’s concerns can help indicate how they would currently prioritize investment in information security.
Knowing your leaders’ biggest priorities in terms of data protection is important for a couple of reasons. First, it can add to your perspective about your company’s most valuable information and the current comfort level in how well it is protected. If you are new to your business, you may not have a clear view yet of the data residing in your organization and the current processes to protect that data.
The other reason it’s important to know your leaders’ priorities is to be able to take that into account when pushing for investment in information security. For example, you may find that your risk in an area like application security doesn’t match up with other leaders’ thoughts about how important it is to prioritize improving it. That’s when you know you need to devote more time to changing perspective.
With all of this in mind, you can start charting out some action items to take care of in the coming months. To know what risks your executives are thinking about, you should periodically ask questions like, “What are your biggest fears right now regarding cyber security?” or, “Based on what I have been sharing, how do you feel about how we are addressing our cyber risk in X area?” Hopefully, these questions lead into broader discussions where you get to weigh in with your knowledge of the current threat landscape and additional risks that may not be currently considered. Once you’ve recognized the areas you need to push more, you need to acquire the means to do so by setting up pipelines for all sorts of metrics. This will take some time, but insightful metrics are the most effective tool you have for communicating risk and needs to leaders of other business areas. As the highest advocate for security, you need to be able to clearly demonstrate when there is a need that needs to be met.
The business’s relationship with information security
An often-overlooked part of information security is the general relationship with security that employees have. Every security professional understands the important role individual employees have in protecting the company from breaches and mistakes that can lead to information leakage. An employee’s relationship security can really be broken down into two parts: awareness and unity.
There are various ways to improve general awareness about security issues as they pertain to different roles. Most companies have some sort of phishing training to build awareness about security because that is something that can affect anyone no matter what their role is. Many companies also have security policies in place that pertain to proper usage of computers; however, it’s equally important to have a way to inform employees about these policies. Automatic labels such as external email address headers and data classification labels are great examples of technical controls that help employees think more critically about the information involved.
Building awareness is important, but successful business security culture also comes from a foundation of support from all groups involved. If you’ve worked in information security for a long time, you probably have your share of stories that include individuals or even whole departments that have a very bad perception of the security team. In many such situations, it comes from past instances where security controls have severely impacted productivity, or maybe security personnel have interacted with employees in a demeaning way which causes them to be defensive. These inconsiderate ways in which a security program is delivered can impact its effectiveness.
As another example of security program effectiveness, consider phishing training. It can be very challenging in practice to be effective at improving these skills over time. Part of the reason is due to lack of engagement from the employees receiving the training. Even if it’s security personnel, there are phish-identifying rockstars out there who rarely, if ever, fail a phishing test. What sets them apart? The answer is they are probably more enthusiastic about security or take phishing training more seriously. Not everyone is inherently interested in information security, so finding creative ways to make security exciting or at least conscious in other departments is paramount in building a successful security culture.
At the end of the day, the information security department must implement controls and programs that are for the good of the company whether they are completely supported or not. However, a little consideration goes a long way in improving employees’ relationships with security. There are some take-away questions from all of this you should be investigating within your organization:
- What security awareness programs do you currently have in place?
- How effective are those programs in driving reduced risk in those areas?
- How aware are your employees of security policies?
- What technical controls can you implement that would increase employees’ consideration of potentially sensitive information?
- What is the business’s general perception of the security team and the current controls you have in place?
- Do you have any controls that severely inhibit productivity?
By answering these questions, you should have identified some things you can start working to improve.
The information security program’s technical maturity
Improving technical maturity is where things can get the busiest. As you could see from the earlier “Map of Cyber Security Domains,” there are many areas of information security that address different types of risk. No one domain is necessarily more important than another. Nevertheless, understanding your organization’s maturity in addressing risk in each of these domains is an important first step as a CISO.
It can be difficult to determine where to begin improving your company’s technical information security, but there are frameworks such as the NIST Cybersecurity Framework or CIS Controls that can help guide you. Cyber security frameworks have their own pros and cons, so you should be mindful about how they are driving your changes.
The biggest benefit of using a cyber security framework is that they help ensure that nothing is overlooked. They provide a holistic guide that, if followed from beginning to end, should produce a very effective information security program. Prioritization is usually built into these frameworks, which makes it easier to decide what to focus on. However, there are some pitfalls when you diligently follow a cyber security framework.
The first pitfall of cyber security frameworks is the “checking boxes” mindset. There are innumerable ways to implement a security control, and they are NOT all equal in effectiveness. Many security software vendors prey on this mindset of plugging a security hole as quickly as possible for the least amount of money. Implementing controls without consideration for residual risk, business culture, and operational efficiency is a recipe for disaster.
The second pitfall of cyber security frameworks is treating security like a destination rather than an evolving entity. As time goes on, your business and cyber security will both change. Frameworks prioritize controls in a relatively effective manner, but they can’t account for every organization’s data protection needs that change or regress over time for various reasons. Without taking this additional context into account, you may find yourself dedicating time and resources to one control while much more cyber risk resides elsewhere. Therefore, it’s important to periodically take inventory of your business’s individual cyber risk — to always know where your priorities need to be.
Advancing your information security program’s technical maturity is where you will probably dedicate the most time as a CISO. This is because of the high volume of projects and action items and the time it takes to implement each one. The first thing you should do is develop your awareness of the data you are trying to protect and the current controls you have in place to protect it. Once you are equipped with that knowledge, you can follow a framework to help guide your well-informed game plan.
Conclusion
Hopefully, you have come away from this piece with a stronger sense of direction and some great new ideas. The biggest takeaway you should have is that information security isn’t just about technical controls. It takes a unified effort across the business to keep information safe. As a CISO, it’s important to be able to understand and empathize with the business side of your role while still advocating for the projects that are needed the most. Your success drives the business’s success, and vice-versa. With a strong security culture as your foundation, you can bring about a lot of positive change for your company’s information security program.